Allow me to tell you a tale. This is the tale of the sysadmin.
You just got hired to work in this small company. The pay could be better, but the staff is very friendly and this goes a long way.
During the interviews you’ve had, you had the opportunity to talk with the current soon to be retired sysadmin. He has seen more than what you could imagine, and carries decades of experience and tales behind his back. Gentle chap, very friendly. You asked how’s documentation, and he assures you that all is documented, and that was the end of the talk.
First day at office! You get your regular welcome onboarding, they show you the house more in-depth and all the good stuff. Sysadmin comes to you and hands you the keys to your very own playground and datacenter. Before you could say thanks, he’s off to a flight to Greenland where he’ll try to start his own business in tomato farming.
And all is dandy and well, until you realize no documentation was handed to you. You asked everyone if any paperwork or file was left for you, only to find nothing. Now you realize that you have deep trouble in your hands. Recon mission to figure all there is to know about this newly aquired network.
After opening with datacenter with a crowbar because they handed you the wrong keys, with the right one nowhere to be found, you finally see, your rack. Your beautiful valuable that you’ll love, hate, love to hate, and won’t trade for anything else.
But now, here’s the dilema: How do you login? This is what we’ll learn today.
To keep in mind that there are more methods to do this than what we could realistically show. So here we’ll show the official Red Hat of resetting the root password.
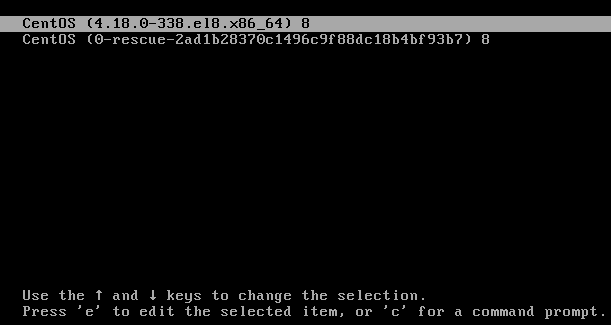
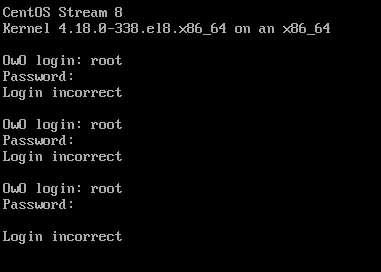
After faced with the password failure, and nowhere near to find what password it is, we restart the server. And here we are presented with GRUB2, our dearly bootloader. This is the beginning of all things. We hover the usual option, bue from here, we hit “e” to edit.
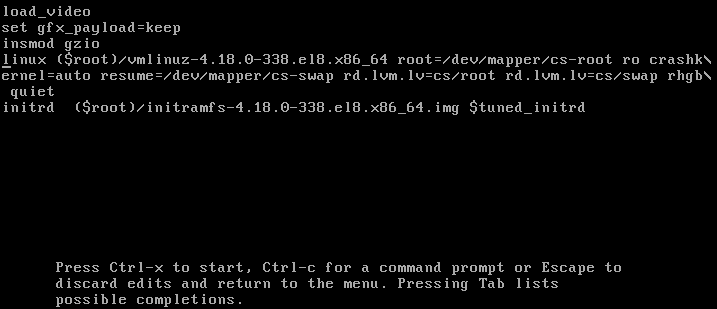
Here we see all arguments used to boot into linux, where’s defined all we need for normal boot.
We don’t want normal boot, we want to spice things up. What do we do? We’ll edit the things just a little.
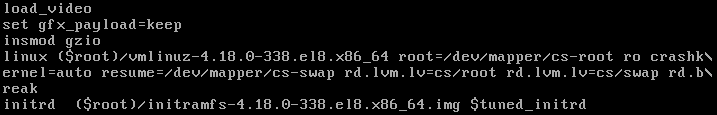
Here we have the line edited. Essentially all we did was change the very end of the linux line. We changed this:
rhgb quiet
To this:
rd.break
Now we do Ctrl-x. Fear not, the changes done here are not ever permanent. For that we would have change the grub config. Not that we would ever need to.
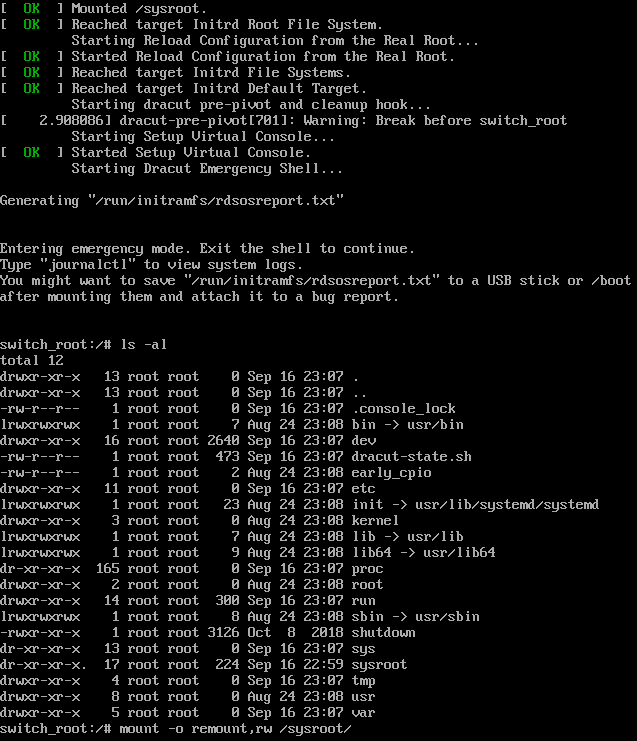
Now we’re welcome to the emergency mode of our kernel. I went ahead and also did a ls -al to show what we’ve got. I also went ahead and wrote the next needed command.
mount -o remount,rw /sysroot
This is rather self explanatory, This is mount options remount, with read and write, this mounting point. This mount point being our entire Operating System.
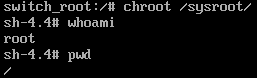
Now we run the following:
chroot /sysroot/
Here now we can see who we are and where we are. Not obligatory commands, but nice to always good to make sure of everything.
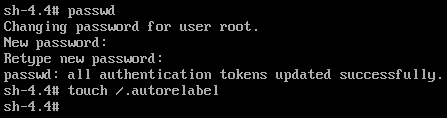
Here now we’re actually changing the password. for that we simply run passwd and give the new password as we want.
We also have another just equally important command.
touch /.autorelabel
As you may or may not figure, this is meant to create an empty file on the root of our system with the name .autorelabel This is a unique step for distros that have SELinux, and enabled. This is the case for distros from the Red Hat family, so it includes RHEL, CentOS, Fedora, and all after related.
Now we do a reboot, no biggie here.
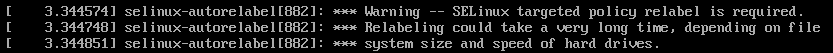
After rebooting and selecting the default option on grub, we have this warning. This was triggered by our empty .autorelabel file. It’s very self-explanatory, but you may miss it on boot, and then get all scared because the server is taking its time to go up.
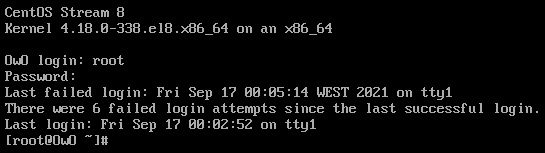
And with this, we have resetted our root password.
Now I can hear Jimmy saying something like “But this is very easy! This is a security flaw! This is why I use the blssed TempleOS.”
And to Jimmy I say: For this to be done, one must be physically connected to the server, or with something like spice for VMs. If a hacker or anyone with bad intentions has PHYSICAL access to your datacenter, you have bigger things to worry about.
Now to address the elephant in the room, yes, I named this machine OwO. I like to trigger a few people (:
See you space cowboy.